Cyber security guidelines for RESOLVD
To improve the efficiency and the hosting capacity of distribution networks in the low voltage grid collecting and processing of vast amounts of different data sets is needed. To achieve this, massively interconnected and smart sensors and actuators are required which in turn exposes the grid to various threats from cyberattacks. The mixture of developed smart components and legacy equipment in particular is a vulnerable combination that needs to be addressed whenever a component is added, changed or removed.
The following figure shows the wide attack surface for cybercriminals in the combined digitized bi-directional power infrastructure of the LV grid.
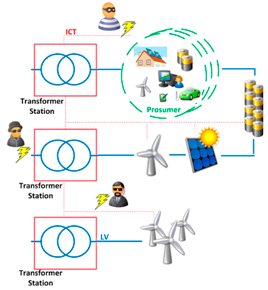
This digitized bi-directional power infrastructure connecting production, distribution and prosumer assets offers the attackers different ways to penetrate the LV Grid via the ICT environment. The so called attack vectors, describing the attack route and the attack technique, can be very diverse depending on the hardware, software, communication channels and physical access. This large attack surface built up by different attack vectors and assets under different ownership has to be carefully addressed. Within RESOLVD this is done by a threat modelling approach to secure the project setup with a systematic security analysis and derived defence mechanism. Therefore the RESOLVD ICT and hardware landscape was modeled with a STRIDE based threat modeling approach influenced by a preceding risk assessment of the different components in use.
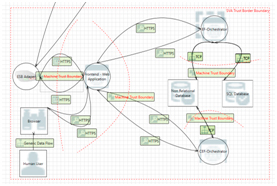
In total 2095 cyber security issues have been identified for the RESOLVD’s system architecture. In order to analyse the identified threats with regards of their applicableness, each component of the RESOLVD project has been analysed in terms of constraints. The review of the constraints has shown that physical access from unauthorized personnel as well as computing intensive operations like state-of-the-art encryption algorithms can be easily handled within a smart grid system. In addition, problems like high latency during communication between each component are addressed by offering high bandwidths (100mbps – 1000mbps) and high availability networks. Regarding the computing power, all devices, including constrained devices, which are devices with limited processing resources like ARM processors and embedded operating systems, are able to handle state-of-the-art encryption algorithms when using cryptographic protocols like TLS.
To mitigate the identified security issues, each threat is addressed within the secure implementation guidelines. for RESOLVD which were assigned to the following categories:
- Upstream Perimeter Security
- Physical Security
- Device Hardening
- Application Hardening
- Device Authentication
- Data Handling
- Communication
JOANNEUM RESEARCH has been in charge of the cyber security guidelines for RESOLVD and a more detailed description can be found in D.4.5 Cybersecurity analysis and recommendations (it’s not available yet).
